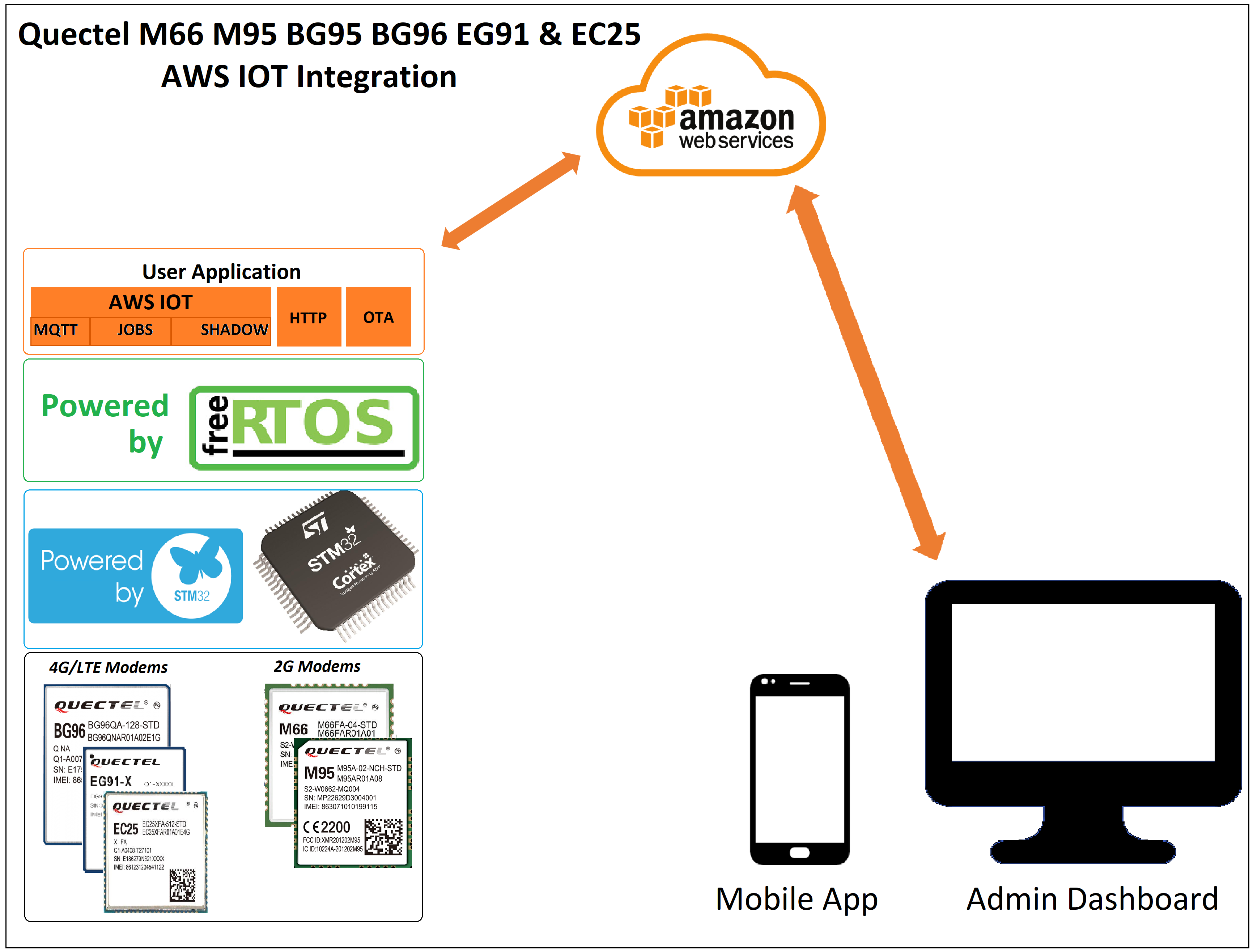
This article covers the integration of Quectel M95 modem with stm32 controller to connect to AWS IOT cloud. The firmware resides on the STM32 and communicates with GSM modem using AT commands.
Features:
- Optimized bootloader to fit in a single sector.
- Data and binary file encryption
- AWS Device Provisioning using a NodeJS script
- AWS IOT MQTT data ingest
- Secure OTA using AWS jobs and S3 bucket
- AWS Shadow updates
Supported Modems
- Quectel M66 — GSM/GPRS module
- Quectel M95 — GSM/GPRS module
- Quectel EG91 — GSM/GPRS module- 4G
- Quectel EG25 — GSM/GPRS module- 4G
- Quectel BG95 — TE Cat M1/Cat NB2/EGPRS
- Quectel BG96 — M1/Cat NB1/EGPRS
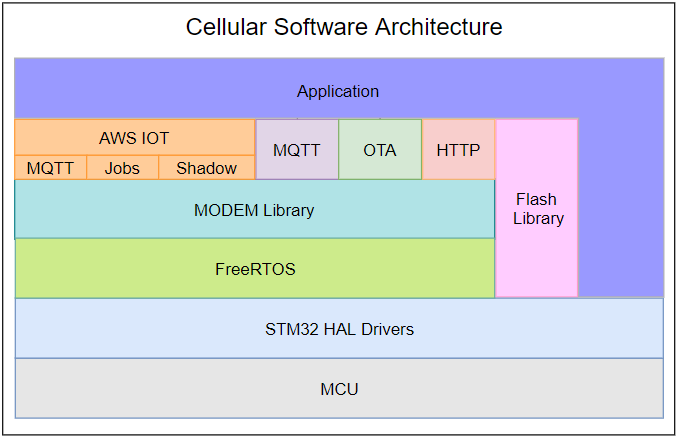
Architecture
Below block diagram shows the firmware architecture of the Quectel cellular solution. The solution is build and tested on Stm32F407 and it can be ported to any of the STM32 controllers with a configuration file.
Software is built on FreeRTOS kernel running two tasks, application and system. System task takes care of AWS IOT, Modem communication, OTA and logging. Application task is completely available for user application.
Requirements
- STM32 Board: The solution is build and tested on STM32F407 Discovery board. It can be customized to run on any of the STM32 controllers.
- Quectel M95 modem: Running on latest firmware at 115200 baud rate.
Project Setup
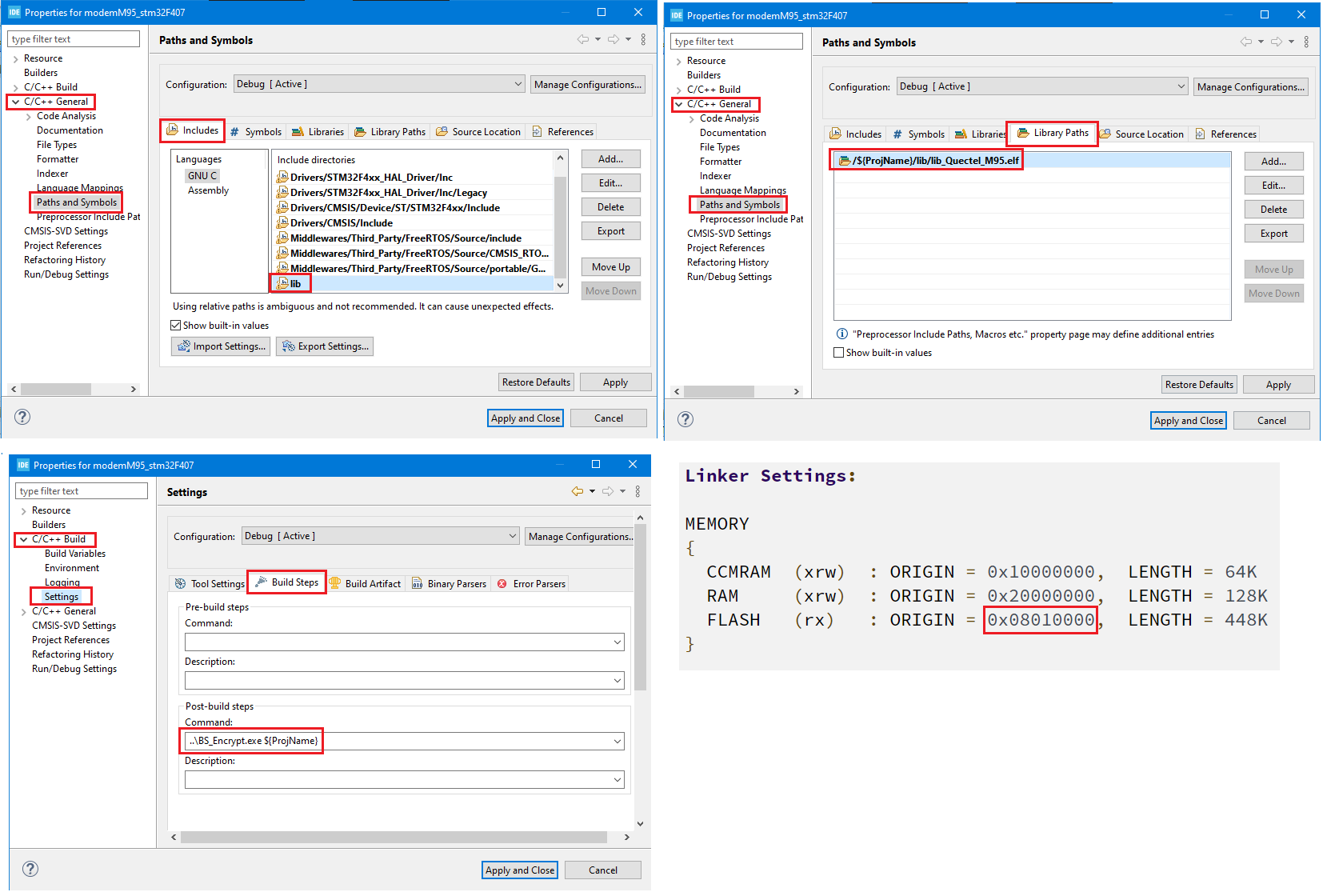
The cellular library is available as precompiled object file with supporting header files under lib folder. These have to be included to the project by following the below steps.
- Include the lib folder containing the library header files to the project.
- Include the precompiled object file to the project.
- Post build script(BS_ENCRYPT.exe) to generate the encrypted application binary file for serial and OTA updates.
- Linker Settings: Application resides at 0x08010000 and same has to be configured in the linker settings as shown below.
Installation
- Download and install stlink_setup.exe, and add the path to environment variables
C:\Program Files (x86)\STMicroelectronics\STM32 ST-LINK Utility\ST-LINK Utility
Connections
- Serial Debug: UART2(PA2, PA3) is used for printing logs and serial firmware updates.
- Modem: UART1(PB6, PB7) is used to communicate with modem at 115200 baud rate.
Test Setup
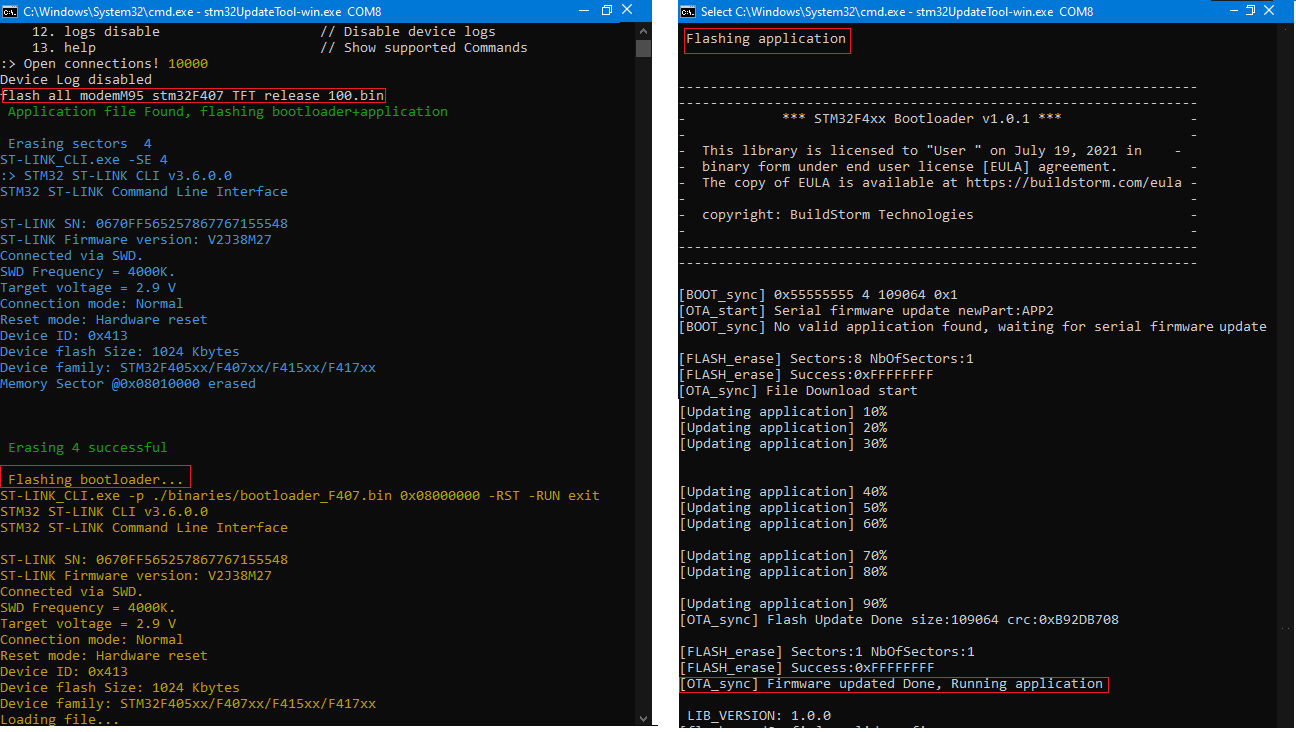
At this point we should have the bootloader and application file that can be flashed to controller. We could use the stLink software to flash the bootloader and serial tools like terminal, putty etc. to send the application file. We also have to register the devices to AWS, download the certificates and send it to device over serial.
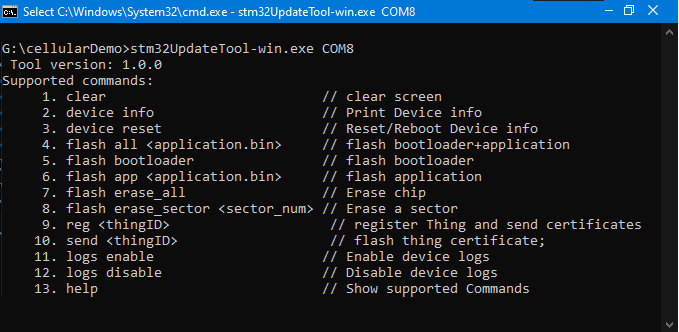
It becomes tedious to use separate tools for all of these during development and most importantly during production. It obvious to put all together in a script and automate the process. The stm32UpdateTool-win.exe is build for the same. It takes care of flashing binaries, registering the devices , send the certificates to device and even deleting the devices.
Below are the steps to setup the command line tool
- Open Command Prompt, change the working directory to the cloned repository.
cd cli-tool - Connect the device using USB-to-serial and note down the COM port.
- Ensure the USB-to-Serial is connected to UART2 of Stm32 (PA2 &PA3).
- Run the command
stm32UpdateTool-win.exe <COM_PORT>
for example, stm32UpdateTool-win.exe COM7 - CLI tool will print the supported commands as shown below.
Flash Bootloader and Application
- Flash both bootloader and application using the flash all command as shown below.
flash all .\binaries\application_v200.bin - CLI will takes care of flashing the bootloader and application one after the other.
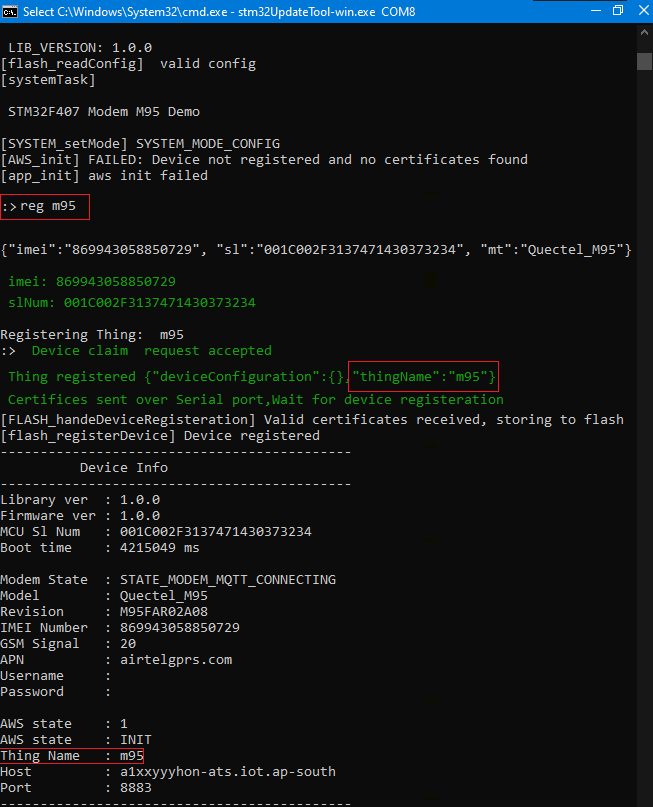
AWS device provisioning
AWS IOT supports provisioning by claim by which the new devices can be registered with unique certificates allocated to each Thing. The CLI tool handles the registering of the things and sends the certificates to the device. Device with store them in the non volatile memory and connect to AWS after a soft reboot.
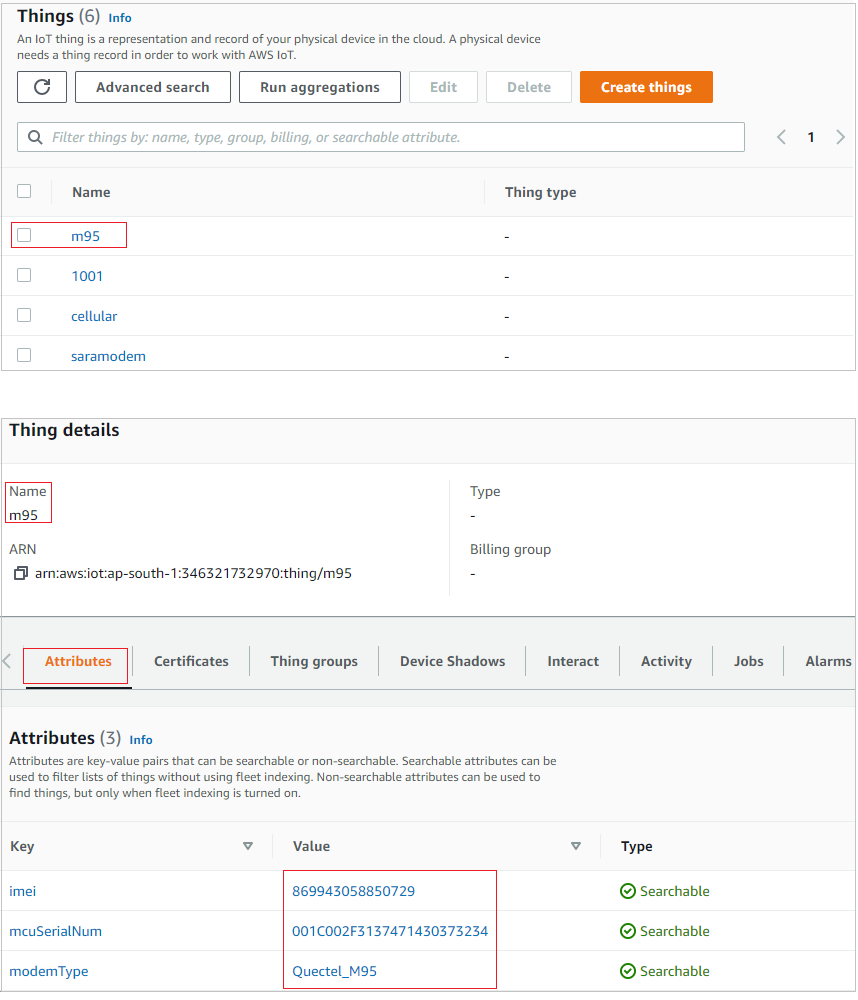
Device Registered on AWS IOT
New device(m95) should be listed on the AWS IOT with unique device attributes.
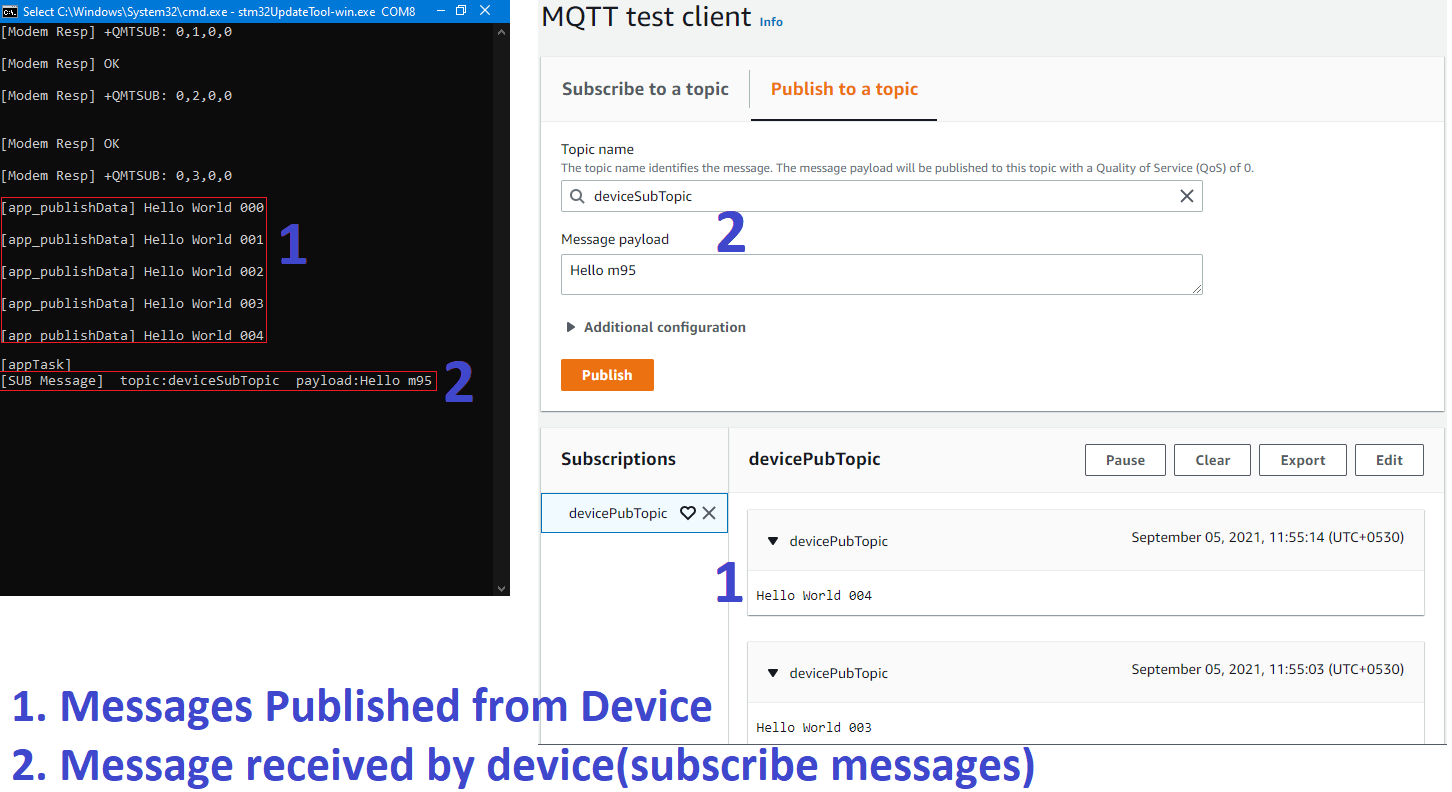
Publish and Subscribe
The sample code publishes the messages to the topic devicePubTopic and receives the messages on the subscribe topic deviceSubTopic.
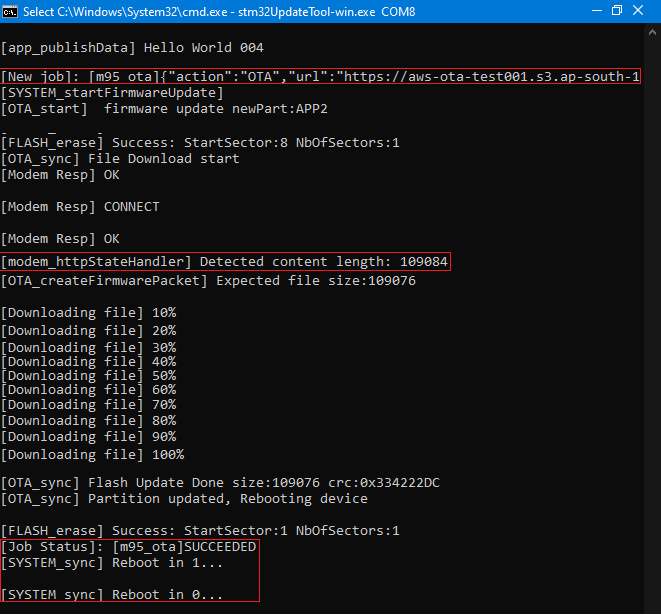
OTA using AWS jobs
We will be using the AWS S3 bucket to store new binaries and AWS jobs to send the OTA update request to each tracker using the Thing Id.
Steps:
- Upload the new firmware to S3 bucket and make the URL public.
- Create the job document with the below format
{"action":"OTA","url":"https://iot-ota-firmware.s3.eu-westamazonaws.com/m95_firmware_release.bin"} - Upload the job document to S3 bucket.
- Send the OTA job request for the Thing using the above job document.
- Device will do the OTA update and send the Failed/Succeed status to AWS jobs. Then it will reboot itself and run the new firmware.
Licensing and Custom Solutions
If you’re looking for a customized solution, reach out at hello@buildstorm.com